I ran into a scenario the other day which I thought would be worth sharing. The customer had a layer 2 trunk link between the SRX firewall and the EX switch was configured so that two VLANs could reach the Internet. Here is the configuration:
SRX:
set interfaces ge-0/0/1 unit 0 family ethernet-switching port-mode trunk
set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members 100
set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members 200
set interfaces vlan unit 100 family inet address 10.10.10.1/24
set interfaces vlan unit 200 family inet address 10.10.20.1/24
set vlans 100 vlan-id 100
set vlans 100 l3-interface vlan.100
set vlans 200 vlan-id 200
set vlans 200 l3-interface vlan.200
EX:
set interfaces ge-0/0/1 unit 0 family ethernet-switching port-mode trunk
set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members 100
set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members 200
set interfaces vlan unit 100 family inet address 10.10.10.2/24
set interfaces vlan unit 200 family inet address 10.10.20.2/24
set vlans 100 vlan-id 100
set vlans 100 l3-interface vlan.100
set vlans 200 vlan-id 200
set vlans 200 l3-interface vlan.200
set routing-options static route 0.0.0.0/0 next-hop 10.10.10.1
Obviously in an ideal scenario, we would not set the environment up this way. Creating a layer 2 trunk between devices while also having layer 3 interfaces on each device will create routing problems. Why? Let's think about the path that traffic destined for the Internet will take for each VLAN...
A host on VLAN 100 (10.10.10.0/24 network) will hit the switch, look at the default route and see a next-hop of 10.10.10.1. Once to 10.10.10.1 (the SRX), traffic will follow that default route out to the Internet. Return traffic will follow the same path back to the host, but with one difference - when the traffic looks at its route table to get back to the host on VLAN 100 (10.10.10.x), it will use the route with the lowest preference. In this case it is a directly connected route to vlan.100, which works fine because it's on the same network.
However, this does not work for VLAN 200, or any other VLAN for that matter. A host on VLAN 200 (10.10.20.0/24 network) will hit the switch, look at the default route and see a next-hop of 10.10.10.1 (which is on a different network). Once to 10.10.10.1 (the SRX), traffic will follow that default route out to the Internet. Return traffic will NOT follow that same path back to the host due to the fact that there is a more preferred route present. In this case as well, there is a directly connected route to the 10.10.20.0/24 network via vlan.200. To illustrate, here is what the route table looks like on the SRX:
10.10.20.0/24 *[Direct/0] 00:00:17
> via vlan.200
Traffic used the default route on the way out and a direct route on the way back. This means that Internet-bound traffic by hosts on VLAN 200 will fail due to asymmetric routing...
There are multiple ways to resolve this issue architecturally, but I thought I would use this scenario as an opportunity to demonstrate the flexibility of routing instances in Junos. We need a way to remove that direct route so that return traffic to the host on VLAN 200 uses the same path that was used on the way out. Here is how it could be accomplished using a routing instance on the SRX:
set routing-instances TEST instance-type virtual-router
set routing-instances TEST interface vlan.200
set routing-options static route 10.10.20.0/24 next-hop 10.10.10.2
By applying this configuration change, we can now see that the direct route is no longer present in the inet.0 route table:
inet.0: 21 destinations, 21 routes (21 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
10.10.20.0/24 *[Static/5] 2d 13:07:42
> to 10.10.10.2 via vlan.234
test.inet.0: 2 destinations, 2 routes (2 active, 0 holddown, 0 hidden)
+ = Active Route, - = Last Active, * = Both
10.10.20.0/24 *[Direct/0] 1d 06:10:43
> via vlan.200
Traffic from a host on the 10.10.20.0/24 subnet now follows the same path in both directions. I want to be clear that the best way to resolve this issue would be to make architectural changes to the network. However, this is a way to "make things work" temporarily, if necessary.
A collection of tutorials, designed to assist systems engineers in the integration of different technical solutions.
Showing posts with label Juniper SRX. Show all posts
Showing posts with label Juniper SRX. Show all posts
Tuesday, November 15, 2016
Wednesday, August 26, 2015
VPN Between a Dell SonicWALL and a Juniper Networks SRX
I have seen multiple people in
forums asking how to setup a site to site VPN between a Juniper SRX
firewall and a Dell SonicWALL firewall. I originally created this post to provide the steps to get things working. I noticed while working with a client that following the old steps no longer work. Below are the revised steps that I took to
get it working, and is based on the following topology:
First we will configure the SRX:
Configure Interfaces:
set interfaces ge-0/0/0 unit 0 family inet address 10.10.10.2/30
set interfaces ge-0/0/1 unit 0 family inet address 192.168.1.1/24
set interfaces st0 unit 0 point-to-point family inet
Configure Routing:
set routing-options static route 172.16.1.0/24 next-hop st0.0
set routing-options static route 0.0.0.0/0 next-hop 10.10.10.1
Configure VPN Parameters:
set security ike policy SRX-TO-SW mode main
set security ike policy SRX-TO-SW proposal-set standard
set security ike policy SRX-TO-SW pre-shared-key ascii-text thisismypsk
set security ike gateway SRX-TO-SW ike-policy SRX-TO-SW
set security ike gateway SRX-TO-SW address 11.11.11.2
set security ike gateway SRX-TO-SW external-interface ge-0/0/0.0
set security ipsec policy SRX-TO-SW proposal-set standard
set security ipsec vpn SRX-TO-SW bind-interface st0.0
set security ipsec vpn SRX-TO-SW ike gateway SRX-TO-SW
set security ipsec vpn SRX-TO-SW ike proxy-identity local 192.168.1.0/24
set security ipsec vpn SRX-TO-SW ike proxy-identity remote 172.16.1.0/24
set security ipsec vpn SRX-TO-SW ike proxy-identity service any
set security ipsec vpn SRX-TO-SW ike ipsec-policy SRX-TO-SW
set security ipsec vpn SRX-TO-SW establish-tunnels immediately
set security flow tcp-mss ipsec-vpn mss 1350
Configure Security Zones:
set security zones security-zone UNTRUST interfaces ge-0/0/0.0
set security zones security-zone UNTRUST host-inbound-traffic system-services ike
set security zones security-zone TRUST interfaces ge-0/0/1.0
set security zones security-zone TRUST host-inbound-traffic system-services all
set security zones security-zone TRUST host-inbound-traffic protocols all
set security zones security-zone VPN interfaces st0.0 host-inbound-traffic system-services all
set security zones security-zone VPN interfaces st0.0 host-inbound-traffic protocols all
Configure Security Policies:
set security policies from-zone TRUST to-zone UNTRUST policy TRUST-TO-UNTRUST match source-address any
set security policies from-zone TRUST to-zone UNTRUST policy TRUST-TO-UNTRUST match destination-address any
set security policies from-zone TRUST to-zone UNTRUST policy TRUST-TO-UNTRUST match application any
set security policies from-zone TRUST to-zone UNTRUST policy TRUST-TO-UNTRUST then permit
set security policies from-zone TRUST to-zone VPN policy TRUST-TO-VPN match source-address any
set security policies from-zone TRUST to-zone VPN policy TRUST-TO-VPN match destination-address any
set security policies from-zone TRUST to-zone VPN policy TRUST-TO-VPN match application any
set security policies from-zone TRUST to-zone VPN policy TRUST-TO-VPN then permit
set security policies from-zone VPN to-zone TRUST policy VPN-TO-TRUST match source-address any
set security policies from-zone VPN to-zone TRUST policy VPN-TO-TRUST match destination-address any
set security policies from-zone VPN to-zone TRUST policy VPN-TO-TRUST match application any
set security policies from-zone VPN to-zone TRUST policy VPN-TO-TRUST then permit
Configure NAT:
set security nat source rule-set TRUST-TO-UNTRUST from zone TRUST
set security nat source rule-set TRUST-TO-UNTRUST to zone UNTRUST
set security nat source rule-set TRUST-TO-UNTRUST rule SRC-NAT match source-address 192.168.1.0/24
set security nat source rule-set TRUST-TO-UNTRUST rule SRC-NAT then source-nat interface
Next we will configure the TZ:
Enable and add a VPN:
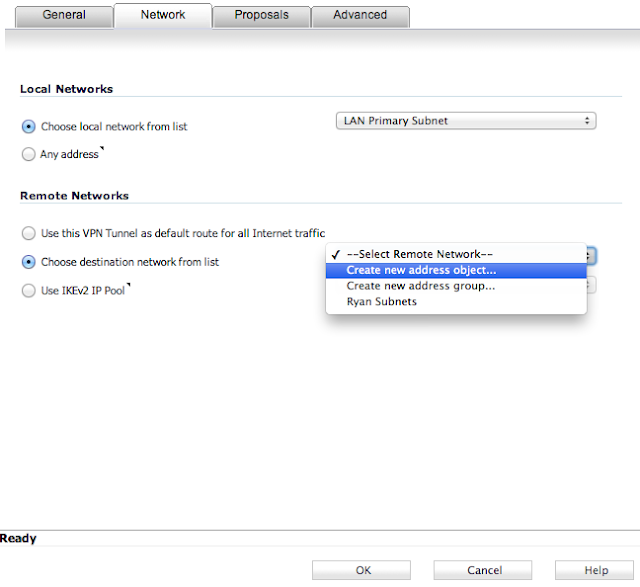
Navigate to VPN->Settings, and then check the box to enable VPN and then click Accept.
Add a new VPN by selecting Add... under VPN Policies on the same page. Enter parameters as shown in the subsequent screenshots for each tab, and then click OK.
That's really it. You can then enable or disable the VPN on the SonicWALL at any time via a checkbox next to the newly created VPN on the VPN->Settings page.
First we will configure the SRX:
Configure Interfaces:
set interfaces ge-0/0/0 unit 0 family inet address 10.10.10.2/30
set interfaces ge-0/0/1 unit 0 family inet address 192.168.1.1/24
set interfaces st0 unit 0 point-to-point family inet
Configure Routing:
set routing-options static route 172.16.1.0/24 next-hop st0.0
set routing-options static route 0.0.0.0/0 next-hop 10.10.10.1
Configure VPN Parameters:
set security ike policy SRX-TO-SW mode main
set security ike policy SRX-TO-SW proposal-set standard
set security ike policy SRX-TO-SW pre-shared-key ascii-text thisismypsk
set security ike gateway SRX-TO-SW ike-policy SRX-TO-SW
set security ike gateway SRX-TO-SW address 11.11.11.2
set security ike gateway SRX-TO-SW external-interface ge-0/0/0.0
set security ipsec policy SRX-TO-SW proposal-set standard
set security ipsec vpn SRX-TO-SW bind-interface st0.0
set security ipsec vpn SRX-TO-SW ike gateway SRX-TO-SW
set security ipsec vpn SRX-TO-SW ike proxy-identity local 192.168.1.0/24
set security ipsec vpn SRX-TO-SW ike proxy-identity remote 172.16.1.0/24
set security ipsec vpn SRX-TO-SW ike proxy-identity service any
set security ipsec vpn SRX-TO-SW ike ipsec-policy SRX-TO-SW
set security ipsec vpn SRX-TO-SW establish-tunnels immediately
set security flow tcp-mss ipsec-vpn mss 1350
Configure Security Zones:
set security zones security-zone UNTRUST interfaces ge-0/0/0.0
set security zones security-zone UNTRUST host-inbound-traffic system-services ike
set security zones security-zone TRUST interfaces ge-0/0/1.0
set security zones security-zone TRUST host-inbound-traffic system-services all
set security zones security-zone TRUST host-inbound-traffic protocols all
set security zones security-zone VPN interfaces st0.0 host-inbound-traffic system-services all
set security zones security-zone VPN interfaces st0.0 host-inbound-traffic protocols all
set security policies from-zone TRUST to-zone UNTRUST policy TRUST-TO-UNTRUST match source-address any
set security policies from-zone TRUST to-zone UNTRUST policy TRUST-TO-UNTRUST match destination-address any
set security policies from-zone TRUST to-zone UNTRUST policy TRUST-TO-UNTRUST match application any
set security policies from-zone TRUST to-zone UNTRUST policy TRUST-TO-UNTRUST then permit
set security policies from-zone TRUST to-zone VPN policy TRUST-TO-VPN match source-address any
set security policies from-zone TRUST to-zone VPN policy TRUST-TO-VPN match destination-address any
set security policies from-zone TRUST to-zone VPN policy TRUST-TO-VPN match application any
set security policies from-zone TRUST to-zone VPN policy TRUST-TO-VPN then permit
set security policies from-zone VPN to-zone TRUST policy VPN-TO-TRUST match source-address any
set security policies from-zone VPN to-zone TRUST policy VPN-TO-TRUST match destination-address any
set security policies from-zone VPN to-zone TRUST policy VPN-TO-TRUST match application any
set security policies from-zone VPN to-zone TRUST policy VPN-TO-TRUST then permit
Configure NAT:
set security nat source rule-set TRUST-TO-UNTRUST from zone TRUST
set security nat source rule-set TRUST-TO-UNTRUST to zone UNTRUST
set security nat source rule-set TRUST-TO-UNTRUST rule SRC-NAT match source-address 192.168.1.0/24
set security nat source rule-set TRUST-TO-UNTRUST rule SRC-NAT then source-nat interface
Next we will configure the TZ:
Enable and add a VPN:
Navigate to VPN->Settings, and then check the box to enable VPN and then click Accept.
Add a new VPN by selecting Add... under VPN Policies on the same page. Enter parameters as shown in the subsequent screenshots for each tab, and then click OK.
That's really it. You can then enable or disable the VPN on the SonicWALL at any time via a checkbox next to the newly created VPN on the VPN->Settings page.
Monitoring the Tunnel:
On the TZ:
You can verify tunnel status by going to VPN->Settings, and looking under Currently Active VPN Tunnels.
On the SRX:
To verify Phase1 is complete, from operational mode issue the following command:
show security ike security-associations
To verify Phase 2 is complete, from operational mode issue the following command:
show security ipsec security-associations
Monday, March 31, 2014
Juniper BGP Over IPSec Multipoint
In my lab, I wanted to utilize a dynamic routing protocol for my hub and spoke VPN topology. I decided to try it with BGP. The requirements were to utilize only one tunnel interface on the hub device for all IPSec tunnels, as well as deny all traffic between spoke sites. Below is the configuration, and it is based on the topology below:
SRX 1 (Hub Device):
Interface configuration (please note that the tunnel interface is configured as multipoint, which allows for the termination of multiple IPSec tunnels to a single logical interface.):
interfaces {
ge-0/0/0 {
unit 0 {
description "*** TRUST ***";
family inet {
address 10.1.1.1/24;
}
}
}
ge-0/0/1 {
unit 0 {
description "*** UNTRUST ***";
family inet {
address 172.16.1.1/30;
}
}
}
lo0 {
unit 0 {
family inet {
address 1.1.1.1/32;
}
}
}
st0 {
unit 0 {
description "*** VPN ***";
multipoint;
family inet {
address 192.168.1.1/24;
}
}
}
}
VPN configuration:
security {
ike {
policy 1-3 {
mode main;
proposal-set standard;
pre-shared-key ascii-text "$9$rV4KWXVwgUjq7-jqmfn6revW7-"; ## SECRET-DATA
}
policy 1-4 {
mode main;
proposal-set standard;
pre-shared-key ascii-text "$9$ZCDH.QF/0BEP5BEcyW8ZUjHP5"; ## SECRET-DATA
}
gateway 3 {
ike-policy 1-3;
address 172.16.3.1;
external-interface ge-0/0/1.0;
}
gateway 4 {
ike-policy 1-4;
address 172.16.4.1;
external-interface ge-0/0/1.0;
}
}
ipsec {
policy 1-3 {
proposal-set standard;
}
policy 1-4 {
proposal-set standard;
}
vpn 1-3 {
bind-interface st0.0;
ike {
gateway 3;
ipsec-policy 1-3;
}
establish-tunnels immediately;
}
vpn 1-4 {
bind-interface st0.0;
ike {
gateway 4;
ipsec-policy 1-4;
}
establish-tunnels immediately;
}
}
Verification:
Here are some commands that can be run from operational mode for verification purposes:
show security ike security-associations
show security ipsec security-associations
show bgp neighbor
show bgp summary
show route
SRX 1 (Hub Device):
Interface configuration (please note that the tunnel interface is configured as multipoint, which allows for the termination of multiple IPSec tunnels to a single logical interface.):
interfaces {
ge-0/0/0 {
unit 0 {
description "*** TRUST ***";
family inet {
address 10.1.1.1/24;
}
}
}
ge-0/0/1 {
unit 0 {
description "*** UNTRUST ***";
family inet {
address 172.16.1.1/30;
}
}
}
lo0 {
unit 0 {
family inet {
address 1.1.1.1/32;
}
}
}
st0 {
unit 0 {
description "*** VPN ***";
multipoint;
family inet {
address 192.168.1.1/24;
}
}
}
}
Default route configuration:
routing-options {
static {
route 0.0.0.0/0 next-hop 172.16.1.2;
}
router-id 1.1.1.1;
autonomous-system 65001;
}
static {
route 0.0.0.0/0 next-hop 172.16.1.2;
}
router-id 1.1.1.1;
autonomous-system 65001;
}
BGP configuration:
protocols {
bgp {
group 1 {
type external;
neighbor 192.168.1.3 {
hold-time 30;
export 1;
peer-as 65003;
local-as 65001;
}
neighbor 192.168.1.4 {
hold-time 30;
export 1;
peer-as 65004;
local-as 65001;
}
}
}
}
Routing policy configuration:
policy-options {
policy-statement 1 {
term 1 {
from {
route-filter 10.1.1.0/24 exact;
}
then accept;
}
term 2 {
from {
route-filter 192.168.1.0/24 exact;
}
then accept;
}
term 3 {
then reject;
}
}
}
bgp {
group 1 {
type external;
neighbor 192.168.1.3 {
hold-time 30;
export 1;
peer-as 65003;
local-as 65001;
}
neighbor 192.168.1.4 {
hold-time 30;
export 1;
peer-as 65004;
local-as 65001;
}
}
}
}
Routing policy configuration:
policy-options {
policy-statement 1 {
term 1 {
from {
route-filter 10.1.1.0/24 exact;
}
then accept;
}
term 2 {
from {
route-filter 192.168.1.0/24 exact;
}
then accept;
}
term 3 {
then reject;
}
}
}
security {
ike {
policy 1-3 {
mode main;
proposal-set standard;
pre-shared-key ascii-text "$9$rV4KWXVwgUjq7-jqmfn6revW7-"; ## SECRET-DATA
}
policy 1-4 {
mode main;
proposal-set standard;
pre-shared-key ascii-text "$9$ZCDH.QF/0BEP5BEcyW8ZUjHP5"; ## SECRET-DATA
}
gateway 3 {
ike-policy 1-3;
address 172.16.3.1;
external-interface ge-0/0/1.0;
}
gateway 4 {
ike-policy 1-4;
address 172.16.4.1;
external-interface ge-0/0/1.0;
}
}
ipsec {
policy 1-3 {
proposal-set standard;
}
policy 1-4 {
proposal-set standard;
}
vpn 1-3 {
bind-interface st0.0;
ike {
gateway 3;
ipsec-policy 1-3;
}
establish-tunnels immediately;
}
vpn 1-4 {
bind-interface st0.0;
ike {
gateway 4;
ipsec-policy 1-4;
}
establish-tunnels immediately;
}
}
}
Security zone configuration (please note that for my lab testing, I am allowing almost everything. In a production environment it is required to enable the necessary services and protocols at the zone level in order for things to function properly (i.e. BGP, IKE, etc.)):
zones {
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
lo0.0;
ge-0/0/0.0;
}
}
security-zone untrust {
screen untrust-screen;
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/1.0;
}
}
security-zone vpn {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
st0.0;
}
}
}
}
Security policy configuration (please note that there is a policy which denies traffic from spoke to spoke):
policies {
from-zone trust to-zone trust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone trust to-zone untrust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone untrust to-zone trust {
policy default-deny {
match {
source-address any;
destination-address any;
application any;
}
then {
deny;
}
}
}
from-zone vpn to-zone vpn {
policy deny-intra-spoke-traffic {
match {
source-address any;
destination-address any;
application any;
}
then {
deny;
}
}
}
from-zone vpn to-zone trust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone trust to-zone vpn {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
}
}
SRX 3 (Spoke Device):
Interface configuration:
interfaces {
ge-0/0/0 {
unit 0 {
description "*** TRUST ***";
family inet {
address 10.3.3.1/24;
}
}
}
ge-0/0/1 {
unit 0 {
description "*** UNTRUST ***";
family inet {
address 172.16.3.1/30;
}
}
}
lo0 {
unit 0 {
family inet {
address 3.3.3.3/32;
}
}
}
st0 {
unit 0 {
description "*** VPN ***";
family inet {
address 192.168.1.3/24;
}
}
}
}
Default route configuration:
routing-options {
static {
route 0.0.0.0/0 next-hop 172.16.3.2;
}
router-id 3.3.3.3;
autonomous-system 65003;
}
static {
route 0.0.0.0/0 next-hop 172.16.3.2;
}
router-id 3.3.3.3;
autonomous-system 65003;
}
BGP configuration:
protocols {
bgp {
group 1 {
type external;
neighbor 192.168.1.1 {
hold-time 30;
export 1;
peer-as 65001;
local-as 65003;
}
}
}
}
Routing policy configuration:
policy-options {
policy-statement 1 {
term 1 {
from {
route-filter 10.3.3.0/24 exact;
}
then accept;
}
term 2 {
from {
route-filter 192.168.1.0/24 exact;
}
then accept;
}
term 3 {
then reject;
}
}
}
bgp {
group 1 {
type external;
neighbor 192.168.1.1 {
hold-time 30;
export 1;
peer-as 65001;
local-as 65003;
}
}
}
}
Routing policy configuration:
policy-options {
policy-statement 1 {
term 1 {
from {
route-filter 10.3.3.0/24 exact;
}
then accept;
}
term 2 {
from {
route-filter 192.168.1.0/24 exact;
}
then accept;
}
term 3 {
then reject;
}
}
}
VPN configuration:
security {
ike {
policy 3-1 {
mode main;
proposal-set standard;
pre-shared-key ascii-text "$9$QATV3/ABIcvWxp0WxNdg4QFn/p0"; ## SECRET-DATA
}
gateway 3-1 {
ike-policy 3-1;
address 172.16.1.1;
external-interface ge-0/0/1.0;
}
}
ipsec {
policy 3-1 {
proposal-set standard;
}
vpn 3-1 {
bind-interface st0.0;
ike {
gateway 3-1;
ipsec-policy 3-1;
}
establish-tunnels immediately;
}
}
}
Security zone configuration:
zones {
security-zone untrust {
screen untrust-screen;
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/1.0;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
lo0.0;
ge-0/0/0.0;
}
}
security-zone vpn {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
st0.0;
}
}
}
}
Security policy configuration:
policies {
from-zone trust to-zone trust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone trust to-zone untrust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone untrust to-zone trust {
policy default-deny {
match {
source-address any;
destination-address any;
application any;
}
then {
deny;
}
}
}
from-zone trust to-zone vpn {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone vpn to-zone trust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone vpn to-zone vpn {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
}
}
SRX 4 (Spoke Device):
Interface configuration:
interfaces {
ge-0/0/0 {
unit 0 {
description "*** TRUST ***";
family inet {
address 10.4.4.1/24;
}
}
}
ge-0/0/1 {
unit 0 {
description "*** UNTRUST ***";
family inet {
address 172.16.4.1/30;
}
}
}
lo0 {
unit 0 {
family inet {
address 4.4.4.4/32;
}
}
}
st0 {
unit 0 {
description "*** VPN ***";
family inet {
address 192.168.1.4/24;
}
}
}
}
Default route configuration:
routing-options {
static {
route 0.0.0.0/0 next-hop 172.16.4.2;
}
router-id 4.4.4.4;
autonomous-system 65004;
}
static {
route 0.0.0.0/0 next-hop 172.16.4.2;
}
router-id 4.4.4.4;
autonomous-system 65004;
}
BGP configuration:
protocols {
bgp {
group 1 {
type external;
neighbor 192.168.1.1 {
hold-time 30;
export 1;
peer-as 65001;
local-as 65004;
}
}
}
}
Routing policy configuration:
policy-options {
policy-statement 1 {
term 1 {
from {
route-filter 10.4.4.0/24 exact;
}
then accept;
}
term 2 {
from {
route-filter 192.168.1.0/24 exact;
}
then accept;
}
term 3 {
then reject;
}
}
}
bgp {
group 1 {
type external;
neighbor 192.168.1.1 {
hold-time 30;
export 1;
peer-as 65001;
local-as 65004;
}
}
}
}
Routing policy configuration:
policy-options {
policy-statement 1 {
term 1 {
from {
route-filter 10.4.4.0/24 exact;
}
then accept;
}
term 2 {
from {
route-filter 192.168.1.0/24 exact;
}
then accept;
}
term 3 {
then reject;
}
}
}
VPN configuration:
security {
ike {
policy 4-1 {
mode main;
proposal-set standard;
pre-shared-key ascii-text "$9$QATV3/ABIcvWxp0WxNdg4QFn/p0"; ## SECRET-DATA
}
gateway 4-1 {
ike-policy 4-1;
address 172.16.1.1;
external-interface ge-0/0/1.0;
}
}
ipsec {
policy 4-1 {
proposal-set standard;
}
vpn 4-1 {
bind-interface st0.0;
ike {
gateway 4-1;
ipsec-policy 4-1;
}
establish-tunnels immediately;
}
}
}
Security zone configuration:
zones {
security-zone untrust {
screen untrust-screen;
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/1.0;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
lo0.0;
ge-0/0/0.0;
}
}
security-zone vpn {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
st0.0;
}
}
}
}
Security policy configuration:
policies {
from-zone trust to-zone trust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone trust to-zone untrust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone untrust to-zone trust {
policy default-deny {
match {
source-address any;
destination-address any;
application any;
}
then {
deny;
}
}
}
from-zone trust to-zone vpn {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone vpn to-zone trust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone vpn to-zone vpn {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
}
}
Verification:
Here are some commands that can be run from operational mode for verification purposes:
show security ike security-associations
show security ipsec security-associations
show bgp neighbor
show bgp summary
show route
Tuesday, January 7, 2014
Juniper OSPF Over IPSec Multipoint
In my lab, I wanted to utilize a dynamic routing protocol for my hub and spoke VPN topology. I decided to first try it with OSPF (BGP configuration here). The requirements were to utilize only one tunnel interface on the hub device for all IPSec tunnels, as well as deny all traffic between spoke sites. Below is the configuration, and it is based on the topology below:
SRX 1 (Hub Device):
Interface configuration (please note that the tunnel interface is configured as multipoint, which allows for the termination of multiple IPSec tunnels to a single logical interface.):
interfaces {
ge-0/0/0 {
unit 0 {
description "*** TRUST ***";
family inet {
address 10.1.1.1/24;
}
}
}
ge-0/0/1 {
unit 0 {
description "*** UNTRUST ***";
family inet {
address 172.16.1.1/30;
}
}
}
lo0 {
unit 0 {
family inet {
address 1.1.1.1/32;
}
}
}
st0 {
unit 0 {
description "*** VPN ***";
multipoint;
family inet {
address 192.168.1.1/24;
}
}
}
}
VPN configuration:
security {
ike {
policy 1-3 {
mode main;
proposal-set standard;
pre-shared-key ascii-text "$9$rV4KWXVwgUjq7-jqmfn6revW7-"; ## SECRET-DATA
}
policy 1-4 {
mode main;
proposal-set standard;
pre-shared-key ascii-text "$9$ZCDH.QF/0BEP5BEcyW8ZUjHP5"; ## SECRET-DATA
}
gateway 3 {
ike-policy 1-3;
address 172.16.3.1;
external-interface ge-0/0/1.0;
}
gateway 4 {
ike-policy 1-4;
address 172.16.4.1;
external-interface ge-0/0/1.0;
}
}
ipsec {
policy 1-3 {
proposal-set standard;
}
policy 1-4 {
proposal-set standard;
}
vpn 1-3 {
bind-interface st0.0;
ike {
gateway 3;
ipsec-policy 1-3;
}
establish-tunnels immediately;
}
vpn 1-4 {
bind-interface st0.0;
ike {
gateway 4;
ipsec-policy 1-4;
}
establish-tunnels immediately;
}
}
Verification:
Here are some commands that can be run from operational mode for verification purposes:
show security ike security-associations
show security ipsec security-associations
show ospf neighbor
show ospf route
SRX 1 (Hub Device):
Interface configuration (please note that the tunnel interface is configured as multipoint, which allows for the termination of multiple IPSec tunnels to a single logical interface.):
interfaces {
ge-0/0/0 {
unit 0 {
description "*** TRUST ***";
family inet {
address 10.1.1.1/24;
}
}
}
ge-0/0/1 {
unit 0 {
description "*** UNTRUST ***";
family inet {
address 172.16.1.1/30;
}
}
}
lo0 {
unit 0 {
family inet {
address 1.1.1.1/32;
}
}
}
st0 {
unit 0 {
description "*** VPN ***";
multipoint;
family inet {
address 192.168.1.1/24;
}
}
}
}
Default route configuration:
routing-options {
static {
route 0.0.0.0/0 next-hop 172.16.1.2;
}
}
OSPF configuration:
protocols {
ospf {
area 0.0.0.0 {
interface ge-0/0/0.0;
interface lo0.0 {
passive;
}
interface st0.0;
}
}
}
security {
ike {
policy 1-3 {
mode main;
proposal-set standard;
pre-shared-key ascii-text "$9$rV4KWXVwgUjq7-jqmfn6revW7-"; ## SECRET-DATA
}
policy 1-4 {
mode main;
proposal-set standard;
pre-shared-key ascii-text "$9$ZCDH.QF/0BEP5BEcyW8ZUjHP5"; ## SECRET-DATA
}
gateway 3 {
ike-policy 1-3;
address 172.16.3.1;
external-interface ge-0/0/1.0;
}
gateway 4 {
ike-policy 1-4;
address 172.16.4.1;
external-interface ge-0/0/1.0;
}
}
ipsec {
policy 1-3 {
proposal-set standard;
}
policy 1-4 {
proposal-set standard;
}
vpn 1-3 {
bind-interface st0.0;
ike {
gateway 3;
ipsec-policy 1-3;
}
establish-tunnels immediately;
}
vpn 1-4 {
bind-interface st0.0;
ike {
gateway 4;
ipsec-policy 1-4;
}
establish-tunnels immediately;
}
}
}
Security zone configuration (please note that for my lab testing, I am allowing almost everything. In a production environment it is required to enable the necessary services and protocols at the zone level in order for things to function properly (i.e. OSPF, IKE, etc.)):
zones {
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
lo0.0;
ge-0/0/0.0;
}
}
security-zone untrust {
screen untrust-screen;
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/1.0;
}
}
security-zone vpn {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
st0.0;
}
}
}
}
Security policy configuration (please note that there is a policy which denies traffic from spoke to spoke):
policies {
from-zone trust to-zone trust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone trust to-zone untrust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone untrust to-zone trust {
policy default-deny {
match {
source-address any;
destination-address any;
application any;
}
then {
deny;
}
}
}
from-zone vpn to-zone vpn {
policy deny-intra-spoke-traffic {
match {
source-address any;
destination-address any;
application any;
}
then {
deny;
}
}
}
from-zone vpn to-zone trust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone trust to-zone vpn {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
}
}
SRX 3 (Spoke Device):
Interface configuration:
interfaces {
ge-0/0/0 {
unit 0 {
description "*** TRUST ***";
family inet {
address 10.3.3.1/24;
}
}
}
ge-0/0/1 {
unit 0 {
description "*** UNTRUST ***";
family inet {
address 172.16.3.1/30;
}
}
}
lo0 {
unit 0 {
family inet {
address 3.3.3.3/32;
}
}
}
st0 {
unit 0 {
description "*** VPN ***";
family inet {
address 192.168.1.3/24;
}
}
}
}
Default route configuration:
routing-options {
static {
route 0.0.0.0/0 next-hop 172.16.3.2;
}
}
OSPF configuration:
protocols {
ospf {
area 0.0.0.0 {
interface st0.0;
interface ge-0/0/0.0;
interface lo0.0 {
passive;
}
}
}
}
VPN configuration:
security {
ike {
policy 3-1 {
mode main;
proposal-set standard;
pre-shared-key ascii-text "$9$QATV3/ABIcvWxp0WxNdg4QFn/p0"; ## SECRET-DATA
}
gateway 3-1 {
ike-policy 3-1;
address 172.16.1.1;
external-interface ge-0/0/1.0;
}
}
ipsec {
policy 3-1 {
proposal-set standard;
}
vpn 3-1 {
bind-interface st0.0;
ike {
gateway 3-1;
ipsec-policy 3-1;
}
establish-tunnels immediately;
}
}
}
Security zone configuration:
zones {
security-zone untrust {
screen untrust-screen;
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/1.0;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
lo0.0;
ge-0/0/0.0;
}
}
security-zone vpn {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
st0.0;
}
}
}
}
Security policy configuration:
policies {
from-zone trust to-zone trust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone trust to-zone untrust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone untrust to-zone trust {
policy default-deny {
match {
source-address any;
destination-address any;
application any;
}
then {
deny;
}
}
}
from-zone trust to-zone vpn {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone vpn to-zone trust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone vpn to-zone vpn {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
}
}
SRX 4 (Spoke Device):
Interface configuration:
interfaces {
ge-0/0/0 {
unit 0 {
description "*** TRUST ***";
family inet {
address 10.4.4.1/24;
}
}
}
ge-0/0/1 {
unit 0 {
description "*** UNTRUST ***";
family inet {
address 172.16.4.1/30;
}
}
}
lo0 {
unit 0 {
family inet {
address 4.4.4.4/32;
}
}
}
st0 {
unit 0 {
description "*** VPN ***";
family inet {
address 192.168.1.4/24;
}
}
}
}
Default route configuration:
routing-options {
static {
route 0.0.0.0/0 next-hop 172.16.4.2;
}
}
OSPF configuration:
protocols {
ospf {
area 0.0.0.0 {
interface st0.0;
interface ge-0/0/0.0;
interface lo0.0 {
passive;
}
}
}
}
VPN configuration:
security {
ike {
policy 4-1 {
mode main;
proposal-set standard;
pre-shared-key ascii-text "$9$QATV3/ABIcvWxp0WxNdg4QFn/p0"; ## SECRET-DATA
}
gateway 4-1 {
ike-policy 4-1;
address 172.16.1.1;
external-interface ge-0/0/1.0;
}
}
ipsec {
policy 4-1 {
proposal-set standard;
}
vpn 4-1 {
bind-interface st0.0;
ike {
gateway 4-1;
ipsec-policy 4-1;
}
establish-tunnels immediately;
}
}
}
Security zone configuration:
zones {
security-zone untrust {
screen untrust-screen;
host-inbound-traffic {
system-services {
ike;
}
}
interfaces {
ge-0/0/1.0;
}
}
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
lo0.0;
ge-0/0/0.0;
}
}
security-zone vpn {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
st0.0;
}
}
}
}
Security policy configuration:
policies {
from-zone trust to-zone trust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone trust to-zone untrust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone untrust to-zone trust {
policy default-deny {
match {
source-address any;
destination-address any;
application any;
}
then {
deny;
}
}
}
from-zone trust to-zone vpn {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone vpn to-zone trust {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone vpn to-zone vpn {
policy default-permit {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
}
}
Verification:
Here are some commands that can be run from operational mode for verification purposes:
show security ike security-associations
show security ipsec security-associations
show ospf neighbor
show ospf route
Subscribe to:
Posts (Atom)