First we will configure the SRX:
Configure Interfaces:
set interfaces fe-0/0/0 unit 0 family inet address 10.10.10.2/30
set interfaces fe-0/0/1 unit 0 family inet address 192.168.1.1/24
Configure Routing:
set routing-options static route 0.0.0.0/0 next-hop 10.10.10.1/30
Configure VPN Parameters:
NOTE: For this specific instance, one of the firewalls is using a dynamic public IP address for its WAN interface, thus the aggressive mode.
set security ike proposal SRX-TO-SW authentication-method pre-shared-keys
set security ike proposal SRX-TO-SW dh-group group2
set security ike proposal SRX-TO-SW authentication-algorithm sha1
set security ike proposal SRX-TO-SW encryption-algorithm aes-256-cbc
set security ike proposal SRX-TO-SW lifetime-seconds 28800
set security ike policy SRX-TO-SW mode aggressive
set security ike policy SRX-TO-SW proposals SRX-TO-SW
set security ike policy SRX-TO-SW pre-shared-key ascii-text thisismypsk
set security ike gateway SRX-TO-SW ike-policy SRX-TO-SW
set security ike gateway SRX-TO-SW address 11.11.11.2
set security ike gateway SRX-TO-SW external-interface fe-0/0/0.0
set security ipsec proposal SRX-TO-SW protocol esp
set security ipsec proposal SRX-TO-SW authentication-algorithm hmac-sha1-96
set security ipsec proposal SRX-TO-SW encryption-algorithm aes-256-cbc
set security ipsec proposal SRX-TO-SW lifetime-seconds 28800
set security ipsec policy SRX-TO-SW proposals SRX-TO-SW
set security ipsec vpn SRX-TO-SW ike gateway SRX-TO-SW
set security ipsec vpn SRX-TO-SW ike ipsec-policy SRX-TO-SW
set security flow tcp-mss ipsec-vpn mss 1350
Configure Security Zones:
set security zones security-zone UNTRUST interfaces fe-0/0/0.0
set security zones security-zone UNTRUST host-inbound-traffic system-services ike
set security zones security-zone UNTRUST address-book address SW-NET 172.16.1.0/24
set security zones security-zone TRUST interfaces fe-0/0/1.0
set security zones security-zone TRUST host-inbound-traffic system-services all
set security zones security-zone TRUST address-book address SRX-NET 192.168.1.0/24
set security policies from-zone TRUST to-zone UNTRUST policy SRX-TO-SW match source-address SRX-NET
set security policies from-zone TRUST to-zone UNTRUST policy SRX-TO-SW match destination-address SW-NET
set security policies from-zone TRUST to-zone UNTRUST policy SRX-TO-SW match application any
set security policies from-zone TRUST to-zone UNTRUST policy SRX-TO-SW then permit tunnel ipsec-vpn SRX-TO-SW
set security policies from-zone TRUST to-zone UNTRUST policy SRX-TO-SW then permit tunnel pair-policy SW-TO-SRX
set security policies from-zone TRUST to-zone UNTRUST policy TRUST-TO-UNTRUST match source-address any
set security policies from-zone TRUST to-zone UNTRUST policy TRUST-TO-UNTRUST match destination-address any
set security policies from-zone TRUST to-zone UNTRUST policy TRUST-TO-UNTRUST match application any
set security policies from-zone TRUST to-zone UNTRUST policy TRUST-TO-UNTRUST then permit
set security policies from-zone UNTRUST to-zone TRUST policy SW-TO-SRX match source-address SW-NET
set security policies from-zone UNTRUST to-zone TRUST policy SW-TO-SRX match destination-address SRX-NET
set security policies from-zone UNTRUST to-zone TRUST policy SW-TO-SRX match application any
set security policies from-zone UNTRUST to-zone TRUST policy SW-TO-SRX then permit tunnel ipsec-vpn SW-TO-SRX
set security policies from-zone UNTRUST to-zone TRUST policy SW-TO-SRX then permit tunnel pair-policy SRX-TO-SW
Configure NAT:
set security nat source rule-set TRUST-TO-UNTRUST from zone TRUST
set security nat source rule-set TRUST-TO-UNTRUST to zone UNTRUST
set security nat source rule-set TRUST-TO-UNTRUST rule SRC-NAT match source-address 192.168.1.0/24
set security nat source rule-set TRUST-TO-UNTRUST rule SRC-NAT then source-nat interface
Next we will configure the TZ:
Enable and add a VPN:
Navigate to VPN->Settings, and then check the box to enable VPN and then click Accept.
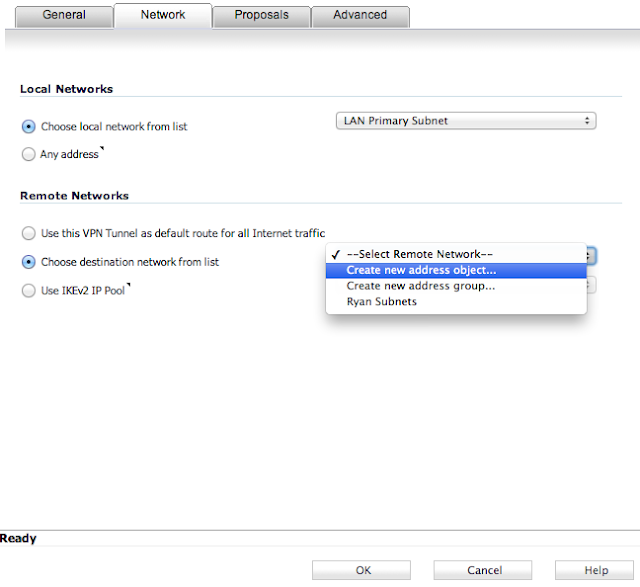
Add a new VPN by selecting Add... under VPN Policies on the same page. Enter parameters as shown in the subsequent screenshots for each tab, and then click OK.
That's really it. You can then enable or disable the VPN on the SonicWALL at any time via a checkbox next to the newly created VPN on the VPN->Settings page.
Monitoring the Tunnel:
On the TZ:
You can verify tunnel status by going to VPN->Settings, and looking under Currently Active VPN Tunnels.
On the SRX:
To verify Phase1 is complete, from operational mode issue the following command:
show security ike security-associations
To verify Phase 2 is complete, from operational mode issue the following command:
show security ipsec security-associations






Great tips given in this blog. I have bookmarked this website and I will keep visiting you for further such interesting posts.
ReplyDeletejuniper srx
Nice topic.
ReplyDeleteThanks for solution.
top10-bestvpn.com
Great solution for Sonicwall and Juniper.
ReplyDeleteIt works good.Nice blog.Thank you.
10webhostingservice.com
There is so much in this article that I would never have thought of on my own. Your content gives readers things to think about in an interesting way. Thank you for your clear information. windscribe free
ReplyDeleteSuper-Duper site! I am Loving it!! Will come back again, Im taking your feed also, Thanks. tor vs vpn
ReplyDeleteIt proved to be Very helpful to me and I am sure to all the commentators here! avast vpn torrenting
ReplyDelete