To elaborate, when a user configures a VPN in an AWS VPC, there is an option to download a VPN configuration for the other side of the tunnel, based on the vendor being used. If Palo Alto Networks is selected, the full configuration in set commands is provided. That stated, the method used for failover to the backup tunnel if the primary tunnel fails is called Policy-based Forwarding (PBF). This is important to note because a PBF configuration does not place routes in the routing table, and therefore there is nothing to inject into OSPF.
If you run into this scenario, rather than configure the tunnelmonitor and PBF features listed in step 4 of the downloaded configuration from AWS, here are the changes that must be made in order to have redundancy work properly:
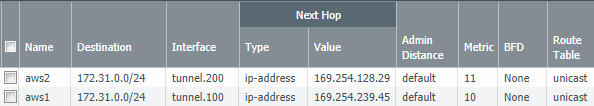
- Create a static route for each tunnel, with a next-hop of the other end of the tunnel subnet. Here are some screenshots of the tunnel interfaces and the associated static routes and path monitoring conditions:
Note that the backup route has a metric set to 11 rather than the default value of 10. This ensures that both routes are in the route table, but the aws2 route only becomes available when the aws1 route is removed from the FIB as a result of the Path Monitoring condition failing.
Failover can be tested by simply disabling the primary tunnel under Network -> IPSec Tunnels -> (select the tunnel) -> Disable.


No comments:
Post a Comment