First we will configure the SRX:
Configure Interfaces:
set interfaces ge-0/0/0 unit 0 family inet address 10.10.10.2/30
set interfaces ge-0/0/1 unit 0 family inet address 192.168.1.1/24
set interfaces st0 unit 0 point-to-point family inet
Configure Routing:
set routing-options static route 172.16.1.0/24 next-hop st0.0
set routing-options static route 0.0.0.0/0 next-hop 10.10.10.1
Configure VPN Parameters:
set security ike policy SRX-TO-SW mode main
set security ike policy SRX-TO-SW proposal-set standard
set security ike policy SRX-TO-SW pre-shared-key ascii-text thisismypsk
set security ike gateway SRX-TO-SW ike-policy SRX-TO-SW
set security ike gateway SRX-TO-SW address 11.11.11.2
set security ike gateway SRX-TO-SW external-interface ge-0/0/0.0
set security ipsec policy SRX-TO-SW proposal-set standard
set security ipsec vpn SRX-TO-SW bind-interface st0.0
set security ipsec vpn SRX-TO-SW ike gateway SRX-TO-SW
set security ipsec vpn SRX-TO-SW ike proxy-identity local 192.168.1.0/24
set security ipsec vpn SRX-TO-SW ike proxy-identity remote 172.16.1.0/24
set security ipsec vpn SRX-TO-SW ike proxy-identity service any
set security ipsec vpn SRX-TO-SW ike ipsec-policy SRX-TO-SW
set security ipsec vpn SRX-TO-SW establish-tunnels immediately
set security flow tcp-mss ipsec-vpn mss 1350
Configure Security Zones:
set security zones security-zone UNTRUST interfaces ge-0/0/0.0
set security zones security-zone UNTRUST host-inbound-traffic system-services ike
set security zones security-zone TRUST interfaces ge-0/0/1.0
set security zones security-zone TRUST host-inbound-traffic system-services all
set security zones security-zone TRUST host-inbound-traffic protocols all
set security zones security-zone VPN interfaces st0.0 host-inbound-traffic system-services all
set security zones security-zone VPN interfaces st0.0 host-inbound-traffic protocols all
set security policies from-zone TRUST to-zone UNTRUST policy TRUST-TO-UNTRUST match source-address any
set security policies from-zone TRUST to-zone UNTRUST policy TRUST-TO-UNTRUST match destination-address any
set security policies from-zone TRUST to-zone UNTRUST policy TRUST-TO-UNTRUST match application any
set security policies from-zone TRUST to-zone UNTRUST policy TRUST-TO-UNTRUST then permit
set security policies from-zone TRUST to-zone VPN policy TRUST-TO-VPN match source-address any
set security policies from-zone TRUST to-zone VPN policy TRUST-TO-VPN match destination-address any
set security policies from-zone TRUST to-zone VPN policy TRUST-TO-VPN match application any
set security policies from-zone TRUST to-zone VPN policy TRUST-TO-VPN then permit
set security policies from-zone VPN to-zone TRUST policy VPN-TO-TRUST match source-address any
set security policies from-zone VPN to-zone TRUST policy VPN-TO-TRUST match destination-address any
set security policies from-zone VPN to-zone TRUST policy VPN-TO-TRUST match application any
set security policies from-zone VPN to-zone TRUST policy VPN-TO-TRUST then permit
Configure NAT:
set security nat source rule-set TRUST-TO-UNTRUST from zone TRUST
set security nat source rule-set TRUST-TO-UNTRUST to zone UNTRUST
set security nat source rule-set TRUST-TO-UNTRUST rule SRC-NAT match source-address 192.168.1.0/24
set security nat source rule-set TRUST-TO-UNTRUST rule SRC-NAT then source-nat interface
Next we will configure the TZ:
Enable and add a VPN:
Navigate to VPN->Settings, and then check the box to enable VPN and then click Accept.
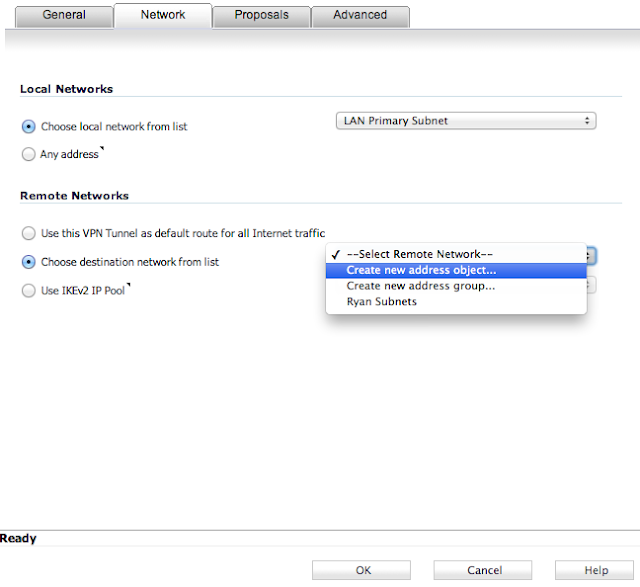
Add a new VPN by selecting Add... under VPN Policies on the same page. Enter parameters as shown in the subsequent screenshots for each tab, and then click OK.
That's really it. You can then enable or disable the VPN on the SonicWALL at any time via a checkbox next to the newly created VPN on the VPN->Settings page.
Monitoring the Tunnel:
On the TZ:
You can verify tunnel status by going to VPN->Settings, and looking under Currently Active VPN Tunnels.
On the SRX:
To verify Phase1 is complete, from operational mode issue the following command:
show security ike security-associations
To verify Phase 2 is complete, from operational mode issue the following command:
show security ipsec security-associations